Post-Roe data risks, BSides consequences and a Russia-Ukraine cyber update

Protesters gather at the Supreme Court on May 2 after POLITICO published a draft opinion revealing the court was preparing to overturn Roe v. Wade. Blake Sobczak/README
Welcome to Changelog for 6/26/22, published by Synack. It’s me, Blake, back after a break for Juneteenth. Thank you to the R Street Institute for hosting me and four cybersecurity experts for a lively discussion Wednesday on the state of water sector cybersecurity. I hope it’s just the first of many successful events in the README and R Street Cyber Policy Talks series. Now, for the week’s news:
The payload
The Supreme Court’s 6–3 ruling overturning Roe v. Wade sent shockwaves through the cybersecurity community, reviving urgent discussions about reproductive rights, digital privacy and the cyber risks facing millions of people affected by the decision.
What once may have been strictly personal data has taken on new significance for anyone needing an abortion in the U.S. Online searches for healthcare services, location and ad tracking data when visiting certain clinics, even information stored by period tracker apps—all of this data will inevitably face additional law enforcement scrutiny in a post-Roe world. The shifting legal landscape has also raised questions about how far prosecutors will go to subpoena information from anyone seeking out-of-state abortion services.
In May, the Electronic Frontier Foundation warned that digital service providers could be flooded with requests to furnish such data in areas where abortion is now illegal.
“Whatever your position on reproductive rights, this is a frightening prospect for data privacy and online expression,” the group noted at the time.
In an updated statement on the Supreme Court’s decision in Dobbs v. Jackson Women’s Health Organization, EFF urged tech companies to take steps like allowing “anonymous access, stopping behavioral tracking, strengthening data deletion policies, encrypting data in transit, enabling end-to-end message encryption by default, preventing location tracking, and ensuring that users get notice when their data is being sought.”
Democratic lawmakers have taken note, though it’s too early to say how post-Roe prosecutions will play out, what a Democrat-controlled Congress may do or how tech companies will respond. But it’s clear that many Americans are facing new fears and dangers when navigating personal healthcare in our highly interconnected lives.
“The difference between now and the last time that abortion was illegal in the United States is that we live in an era of unprecedented digital surveillance,” EFF’s director of cybersecurity Eva Galperin said on Twitter.
The week, compiled
The Russia-Ukraine war’s cybersecurity impacts have evaded easy classification. What does “cyberwar” mean in the context of a ground war where tens of thousands of people have been killed from bombs and gunfire? Did Russia’s use of “wiper” data-destroying cyberattacks really test Ukraine’s defenses?

“While it’s possible to find encouragement in either some Russian missteps or early triumphs of defensive technology, the easiest and biggest mistake would be to declare a premature victory,” Microsoft cautioned in a new report on “Lessons from the Cyber War” in Ukraine. “Wars are won over time, setbacks can be reversed, and Russian agencies have long invested in sophisticated cyber tactics and techniques.”
Many of the action items in Microsoft’s update will come as no surprise to readers of its last dispatch on Russia-Ukraine cyber operations in April, like the need for stronger cyber detection capabilities to spot anomalies that could expose Russian hackers. But in its latest report, the company also called for developing a strategic, coordinated international response to Russian disinformation and highlighted the need to build a better capacity to detect foreign influence operations. Microsoft even got a bit meta in its analysis of the cyber war:
“The fact that this report is authored by a company is clear evidence of the inevitable role that the technology sector plays in the cyber defense of nations in the world today,” the company said.
Here’s what else played out last week:
The Washington Post: Ace cybersecurity reporter Joe Marks penned his last newsletter at The Cybersecurity 202 after three and a half years on the job. The upshot: Things will get worse before they get better. “The cyber future is especially treacherous because of a number of powerful new technologies that will integrate the internet ever more deeply into the fabric of daily life — including 5G wireless networks, artificial intelligence and connected technologies such as smart thermostats,” Marks wrote.
Port Swigger: BSides Cleveland organizer Rockie Brockway stepped down from his role organizing the infosec event after a controversial decision to host Chris Hadnagy as a surprise speaker at the confernece. Hadnagy has been banned from DEF CON for alleged code of conduct violations.
CyberScoop: The Cybersecurity and Infrastructure Security Agency’s Cybersecurity Advisory Committee issued a slate of recommendations aimed at improving the agency’s handling of pressing cybersecurity challenges like election security and effective vulnerability disclosure.
Protocol: The cybersecurity sector could face a wave of business consolidation as the economy slows down and “tool sprawl” starts to grate on CISOs.
A message from Synack
Synack Red Team mission data indicates that once-a-year pentests are no longer adequate to protect sensitive missions or meet most compliance requirements. Government Agencies Deserve A Better Way To Pentest, one that scales to find vulnerabilities that matter most and to meet M-22–09 zero trust requirements for dedicated application security testing. Find your Better Way to Pentest today in Synack’s FedRAMP Moderate In Process environment.
Flash memory
On Jan. 13, 2018, Hawaii residents got a rude Saturday morning awakening when their phones sounded this warning:
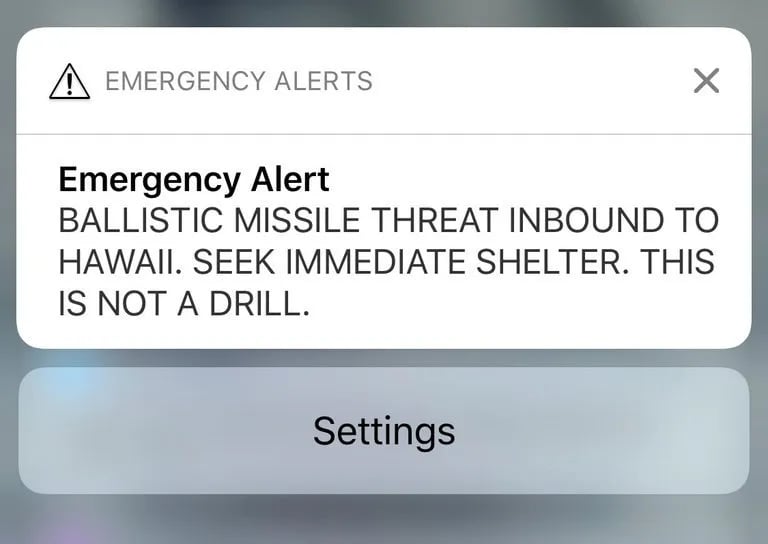
It was a false alarm — one caused by a combination of user error and stunning design failures of the state’s emergency response systems, as The Verge reported at the time. But the episode raised questions about the architecture and cyber defenses of such computer networks.
I was reminded of the Hawaii snafu because last week, missile sirens sounded in parts of Jerusalem and in the Israeli port town of Eilat after a suspected hack of public address systems, Haaretz reported. It’s a literally alarming example of a cyberattack — in this case, possibly an Iran-linked campaign — that sets out to stoke fear.
Local files
BBC News: In Amagasaki, Japan, an unnamed man managed to lose personal information for the entire city’s population after misplacing a USB stick following a soused night out with colleagues. The data is reportedly encrypted and the drive was later recovered, but still…
Reuters: Google called out Milan-based RCS Lab for selling spyware used to hack Android devices and other smartphones in Italy and Kazakhstan, warning of the “proliferation of dangerous hacking tools.”
WTKR [Norfolk, Va.]: Two suspects were arrested earlier this month in connection with what one cybersecurity professor described as a “highly sophisticated” scheme to steal gasoline from hacked pumps.
Off-script
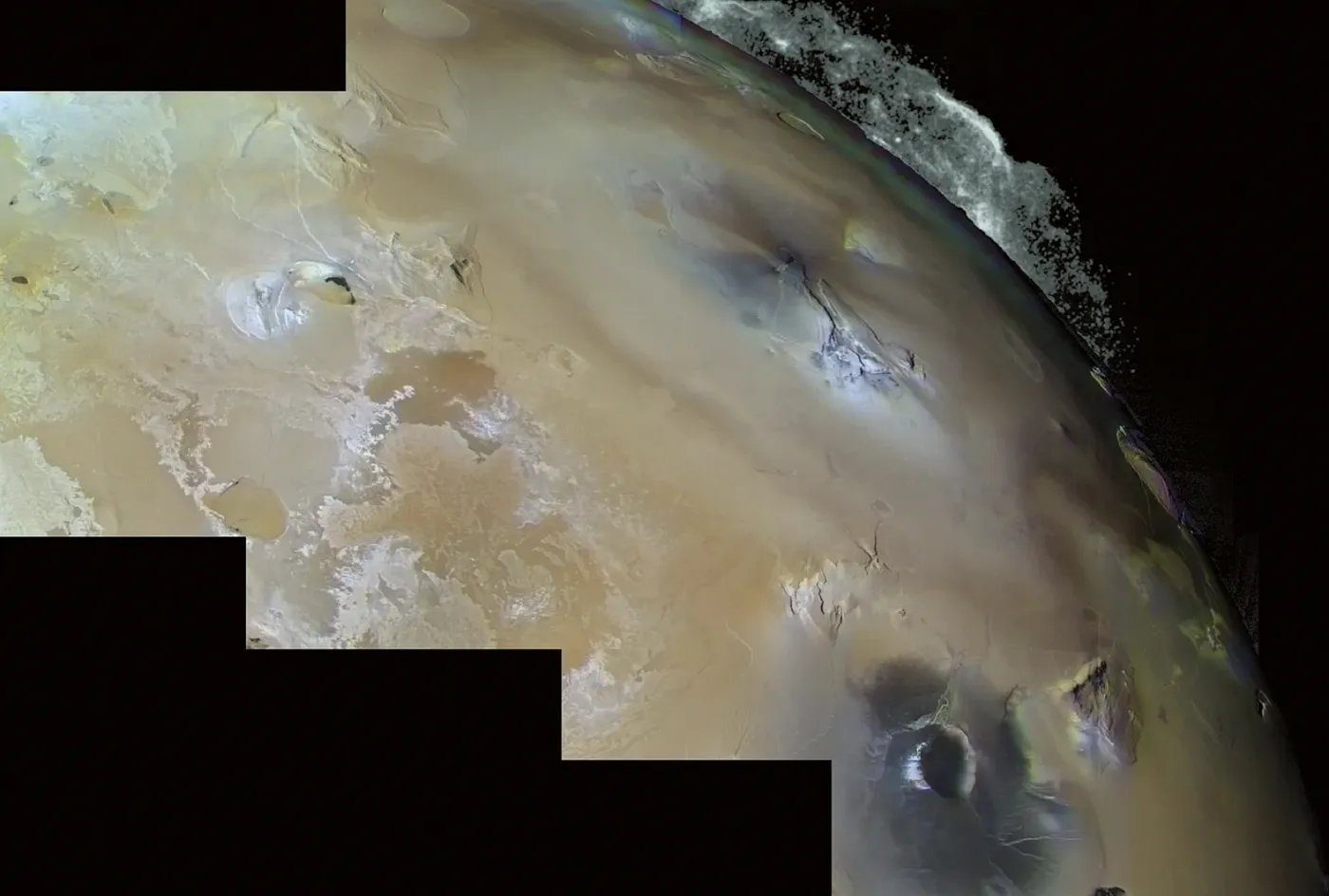
The pioneering Voyager 1 and Voyager 2 spacecraft, launched nearly 45 years ago, are on the verge of powering down for good, according to an in-depth report by Scientific American.
What a trip they’ve had! Voyager 1 became the first spacecraft to venture into interstellar space in 2012, and its hardwired sibling followed it shortly thereafter. They’ve captured a raft of invaluable data and incredible images from our galaxy, like the composite below of Jupiter’s moon, Io.
The good news is — even if their few remaining instruments stop beaconing home — both Voyagers are slated to outlast Earth in their cold journey through the cosmos.
That’s it for now. Please send feedback or tips to bsobczak@synack.com — see you next week!







