Sandworm’s kingpin, a CISA ransomware pilot and pandemic scams

Evgenii Serebriakov is reportedly the leader of Russia’s infamous Sandworm hacking unit. U.S. Justice Department
Welcome to Changelog for 3/19/23, published by Synack! Blake here, basking in the annual D.C. tradition of peak cherry blossom bloom. I’ll jog around the Tidal Basin later this afternoon to soak up the views, but for now, here’s the week’s cyber news:
The payload
The notorious Sandworm hacking group is known for launching spearphishing attacks on the 2018 Winter Olympics, briefly knocking out power to parts of Ukraine’s grid in the mid-2010s, and generally causing mayhem by deploying destructive malware worldwide. (The Sandworm-orchestrtaed NotPetya cyber disaster cost an estimated $10 billion in damages globally back in 2017.)
It’s an ignominious crew affiliated with Unit 74455 of the Russian Main Intelligence Directorate (GRU). Sandworm has spread wiper malware against Kyiv throughout the Russia-Ukraine war. But despite U.S. Justice Department indictments and near-constant press attention, Sandworm’s leader has stayed shrouded in anonymity — until now.
Wired reported Wednesday that Evgenii Serebriakov is Sandworm’s commander as of spring 2022, evidently securing the promotion despite participating in a brazen, botched 2018 cyberespionage operation against the Organization for the Prohibition of Chemical Weapons in the Netherlands. (Dutch law enforcement officials deported Serebriakov in that case. The latest revelations may make it even harder for the Russian intelligence official to do much European sightseeing.)
Experts at the open-source intelligence group Bellingcat backed up Wired’s findings, which were also confirmed by an unidentified Western intelligence official.
The fact that Serebriakov is already a familiar face to close watchers of Russian cyberthreats speaks to the fact that even foreign adversaries may have trouble recruiting and retaining cyber talent.
“We’re still living in a world where talent is apparently limited to the point where we know the adversaries intimately,” John Hultquist, head of threat intelligence at Google subsidiary Mandiant, told Wired.
The week, compiled
The Cybersecurity and Infrastructure Security Agency is forging ahead with a congressionally-mandated program aimed at combatting incessant ransomware threats.
The Ransomware Vulnerability Warning Pilot (RVWP) officially kicked off in January, but CISA shared new details of the early warning program last week, as Cybersecurity Dive reported.
The goal is to tip off organizations that don’t know their networks have vulnerabilities known to be exploited by ransomware groups.
To get the word out, CISA will rely on its subpoena authorities so it can tie vulnerable software it spots online back to specific organizations participating in the program.

“By urgently fixing these vulnerabilities, organizations can significantly reduce their likelihood of experiencing a ransomware event,” CISA said. (Notably, organizations aren’t required to fix vulnerabilities that CISA points out.)
Here’s what else happened last week:
The Wall Street Journal: The Securities and Exchange Commission is proposing a bevy of new cybersecurity rules that would require brokers and asset managers to notify customers of a breach within 30 days, among other changes. The rules are now up for public comment before the SEC finalizes them.
Cointelegraph: An attacker siphoned off $197 million in cryptocurrency from Euler Finance, which has since offered a $1 million reward for information on the hacker. Strangely, the unknown assailant returned some 3,000 Ether (worth over $5 million) to Euler over the weekend, but the breach still stands as the biggest crypto heist of 2023 so far.
CyberScoop: Buckle up: Microsoft is warning Russia may be prepping a wave of destructive cyberattacks that could spill beyond Ukraine’s borders. “It is not that we necessarily think that Russia will launch a stream of cyberattacks, however we are currently seeing patterns of targeted threat activity in Ukraine similar to the early days of the invasion,” Microsoft official Clint Watts told CyberScoop.
A message from Synack
Insecure and unmanaged APIs can lead to multimillion-dollar security incidents, according to Gartner. Join Synack co-founder and CTO Mark Kuhr and Sabre application security principal Cris Rodriguez for a webinar to learn of a better way to pentest for APIs. They break down the top API vulnerabilities and share best practices for securing this critical part of organizations’ attack surfaces. Learn more and view the webinar on demand here.
Flash memory
Three years ago, the COVID pandemic started disrupting daily life in North America, forcing office closures and event cancellations while putting medical professionals on high alert.
Scammers were quick to capitalize on the emergency, as Mandiant reported in a threat research update at the time.
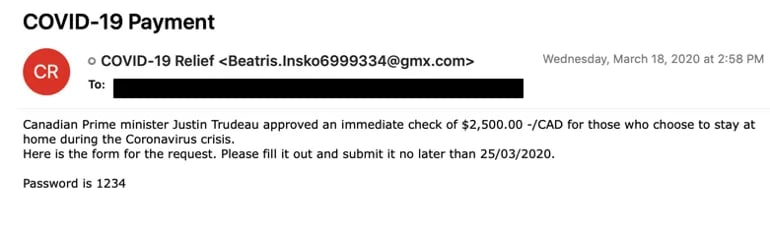
As governments kicked into high gear to disburse COVID relief funds, cybercriminals and scammers shifted tactics.
“Malicious actors have always exploited users’ sense of urgency, fear, goodwill and mistrust to enhance their operations,” Mandiant said. “The threat actors exploiting this crisis are not new, they are simply taking advantage of a particularly overtaxed target set that is urgently seeking new information.”
Local files
The Lansing State Journal: Lansing Community College was forced to cancel classes last week after suffering an unspecified “cybersecurity incident.” Disruptions from the incident are expected to carry on for several more days, and the FBI is helping the school to investigate.
The Record: The U.K. has spun up a new agency to address Chinese intellectual property theft and other security threats. Officials said the National Protective Security Authority (NPSA), part of the country’s MI5 domestic intelligence agency, will work closely with the National Cyber Security Centre to provide security trainings and other resources for organizations contending with state-sponsored IP theft.
CISA: The top U.S. civilian cybersecurity agency has joined forces with the Girl Scouts in a bid to bridge the gender gap in cybersecurity, inking a memorandum of understanding that will see the groups participate in conventions together and continue to support initiatives like cybersecurity skills badges. I can only hope CISA will formally designate Girl Scout Cookies as critical infrastructure.
Off-script
I’m hardly a fan of March Madness — I didn’t even enter Synack’s friendly office bracket — but I cheered for my alma mater Northwestern University as they competed in the big dance for the second time ever.
After defeating Boise State 75–67 on Thursday, №7 seed Northwestern fell to UCLA in the second round in an intense 68–63 battle. Congrats on a hard-fought season!

That’s all for this week — don’t forget to send tips and feedback to bsobczak@synack.com. See you next Sunday!







