As APIs proliferate, attackers follow
With APIs accounting for more than half of all internet traffic, attacks on mobile and web application endpoints continue to grow.
On January 5, cellular telecommunications firm T-Mobile discovered a large volume of anomalous requests hitting an unprotected application programming interface (API), mining sensitive information such as customers’ names, addresses, emails, phone numbers and dates of birth.
The attack abused the API to siphon off data about approximately 37 million T-Mobile customers over the course of six weeks before the firm discovered the activity. The company tracked down the source of the traffic and closed the hole within a day, but the damage had been done.
“We currently believe that the bad actor first retrieved data through the impacted API starting on or around November 25, 2022,” T-Mobile warned investors in a regulatory filing that included details of the breach. “We may incur significant expenses in connection with this incident.”
As application development has moved to cloud-native applications using microservices, APIs have become the primary way to link software services and build applications. The trend has resulted in a wholesale shift to APIs. In 2022, the majority of internet traffic (55%) was API-related, slightly up from the 54% of internet traffic related to APIs in December 2021, according to the latest data from internet infrastructure firm Cloudflare.
Companies that inventory their APIs traffic — and 73% do so in an automated way, according to a survey by S&P Global Market Intelligence — have seen an explosion in the number of API requests. In 2022, the average organization’s applications requested information from more than 15,000 API endpoints, triple the number discovered in 2021, according to the survey.
Attackers have followed. More than nine in 10 companies (92%) have acknowledged at least one API-related security incident in the past 12 months, with 57% of companies experiencing multiple incidents, according to a survey by the Enterprise Strategy Group (ESG).
“Organizations are modernizing their development processes, and APIs are just proliferating, … connecting microservices to microservices and connecting to integrations,” Melinda Marks, a senior analyst with ESG, told README. “[Companies] want to build better features and functionality for their customers, which means more APIs, but if they don’t take into account the security implications, it just adds up to more exposure to attack.”
Rogue APIs are proliferating
A major driver of the proliferation of APIs and the lack of security around the application architecture is the move to more agile development methodologies, such as DevOps, and cloud deployment. While these approaches to development are considered best practices, they must be paired with security education and tools to prevent insecure code from being pushed to production. More than half of companies (57%) use DevOps extensively, and 80% use APIs in all, or most, of their applications, according to the ESG report.
Companies typically “own” at least dozens or hundreds of APIs internally, with developers using those application endpoints in architecting their software. Six-in-ten small companies use 10 internal APIs, for example, while nearly 40% of large companies use 250 or more APIs, according to software development firm RapidAPI’s 2022 State of APIs report. Three-quarters of companies (76%) use at least 26 APIs per application that they deploy, according to the ESG report.
Yet developers often fail to properly document or secure their APIs, creating shadow, or rogue, APIs. Almost half (48%) of organizations have released known-vulnerable applications because of time constraints, according to ESG.
The result is that attackers are always on the lookout for APIs that can be abused in unintended ways — in some cases, getting access to extremely sensitive functionality or data, Patrick Sullivan, chief technology officer at internet infrastructure firm Akamai, told README.
“Rather than kind of traditionally having a single monolithic app, there are now tons of these APIs, and if there is any breakdown in the process, there’s often a direct path to business logic there, and those [sorts of security holes] can be the most devastating,” he said.
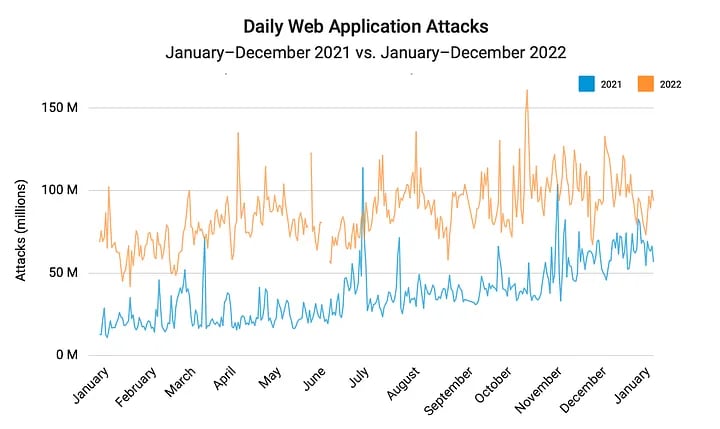
The extensive use of APIs has led to an increase in attack traffic targeting service endpoints. In 2022, the amount of attacks targeting APIs grew by 150%, with a peak of 161 million daily attacks in October, according to Akamai’s The Rise of Application and API Attacks report.
Malicious abuse or unwanted attention?
Among the most popular attacks on APIs, credentials stuffing uses authentication APIs to quickly cycle through legitimate credentials or conduct a brute force effort guessing common passwords. A typical attack may be a hundred thousand requests from hundreds of IP addresses in a 24-hour period, Jason Kent, a hacker-in-residence at Cequence Security, told README.
“Account takeover is kind of the bread and butter — it’s sort of the primary thing that happens if you have a site that you log into, and you have rewards points, or you make purchases through that, or whatever,” he said. “Somebody wants to get your credentials and either take your rewards points or purchase something as you or they may just actually need the account because they’re doing something else.”

In May, credential stuffing attacks were at the heart of a Federal Trade Commission order that would block Amazon’s Ring division from profiting from doorbell and security camera videos that the company failed to protect against hackers. The agency ordered Amazon to pay nearly $5.8 million in refunds to the 55,000 customers who were impacted by those attacks, as well as by employees illicitly using administrative access, the FTC said in a statement.
Another popular API attack is Local File Inclusion (LFI), which uses a request to a web application to expose, and sometimes run, files on the server. Attackers have used LFI attacks for reconnaissance and to scan for vulnerable servers, resulting in the attack category driving growth in API attacks, Akamai said in its report.
But not all API attacks lead to a data breach or remote execution. Denial-of-service (DOS) attacks are quite common, but often attempt to use the functionality accessed by an API call to perform a resource exhaustion attack on the application. Finally, more benign — but sometimes just as impactful — attacks, such as data scraping, can be used by competitors to gain a leg up on their rivals.
“If you have a competitor that is scraping your data in such a way that it’s generating an outcome that the business doesn’t want, and they’re sort of abusing that API that’s been extended, we would consider that malicious,” said Akamai’s Sullivan.
Shed light on shadow APIs
Often, APIs are not properly protected because the security team does not know they exist. These shadow APIs, or rogue APIs, represent an unknown attack surface that attackers often find before companies do.
For that reason, defenders need to start with visibility, discovering all new APIs, the undocumented shadow APIs, the rogue APIs, and APIs from partners who may not have fully documented the interface. The software development cycle needs to include fully documenting APIs, even if they are considered internal and not accessible to the internet, said Akamai’s Sullivan.

“Probably most organizations have some level of exposed APIs that security is not tracking, or [of which] they don’t have that awareness,” he said. “These are their shadow APIs, their zombie APIs, that were created and now the developer has moved on, but the API persists, leaving that full lifecycle at risk.”
Defenders also need to analyze incoming API requests for signs of attacks or fraud. Anomalous traffic from a single IP, or similar traffic from a collection of IPs, can both be indicative of an attack, Prakash Sinha, a senior director and evangelist at security firm Radware, told README.
“You have to have some kind of protection in the cloud, because the attacker is trying to put the cost of an attack on you,” he said. “If you can flip the script and ask [the user’s machine] to solve a problem — we do it with blockchain technology — then the onus is on the client to prove they are not malicious.”
A good place to start is the OWASP API Security Top-10 list — the latest version of which came out this month — and make sure to adopt defenses against those common issues, Sinha said. Web application firewalls and API security measures can also help protect applications at run time.
Yet, perhaps the best place to start is with developers, ESG’s Marks said.
“The more that developers are empowered and have the right tools in place to do testing in a way that does not slow development down, the better,” she told README. “Security needs to pick the right tools and help developers get the right tools and processes in place, so that developers are able to take an active part in securing their own code and their APIs.”







