Robert Lemos
README | Robert Lemos
April 12, 2024
A sudden halt to the ranking of vulnerability severity has left government agencies and some companies without an approved source of ranking and prioritization.
February 05, 2024
Despite forecasts of healthy demand for cybersecurity skills, workers see more cuts and a more intense hiring process in their futures.
December 21, 2023
In 2023, attackers continue to wield more zero-day exploits against companies and individuals, using them for ransomware, surveillance and espionage.
December 13, 2023
CVSS 4.0 urges companies to go beyond base scores, allowing them to more accurately judge the threat posed by particular vulnerabilities.
November 15, 2023
Developers must be increasingly wary of actively malicious code that makes its way into their software supply chains.
October 18, 2023
When attackers find vulnerabilities in software used by service providers with dozens or hundreds of clients, the impact of a breach can quickly spiral out of control.
September 27, 2023
The U.S. government and technology giants alike are urging developers to replace C and C++ with modern, memory-safe languages like Rust. Will it be enough?
September 13, 2023
At least one person has died as what was arguably the direct result of a digital attack on a hospital, but cybercriminals seem unlikely to stop.
August 25, 2023
Deepfakes, stolen email addresses and identity fraud drive continued gains in business email compromise attacks. How can defenders fend them off?
July 18, 2023
VPNs, virtualization hosts, secure email gateways and other network “edge” devices have become a common entry point for attackers in significant enterprise breaches. How can defenders respond?
June 13, 2023
With APIs accounting for more than half of all internet traffic, attacks on mobile and web application endpoints continue to grow.
May 30, 2023
AI dominated conversations at the RSA Security Conference in May, but underneath the hype, some real changes are in the works.
May 09, 2023
Increases in phishing attacks, credential stuffing against corporate cloud services and unpatched vulnerabilities in consumer hardware have all skyrocketed since the COVID pandemic upended work routines. With more employees logging in from home, locking down workers’ security habits and local networks has never mattered so much.
April 17, 2023
While the open-source ecosystem continues to make progress on securing the production of widely used components, developers need better tools and a security culture to benefit.
March 10, 2023
The global cyberthreat landscape has changed since Russia’s invasion of Ukraine but not necessarily in the ways predicted.
February 03, 2023
Multiple studies have found that generative neural networks that produce code also reproduce security vulnerabilities in their datasets.
December 01, 2022
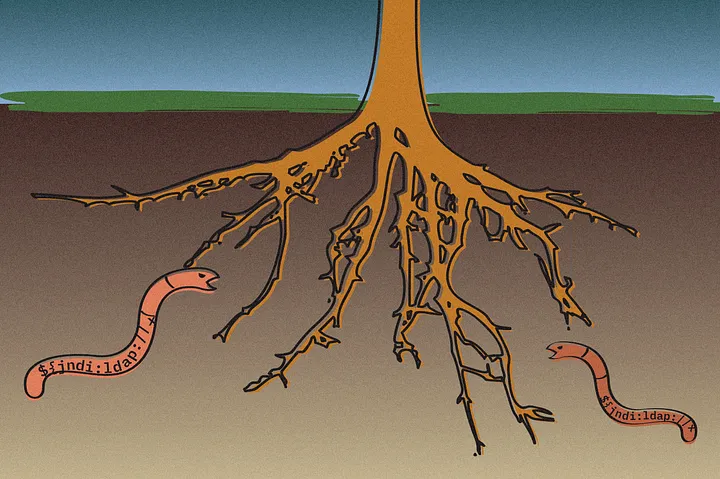
The fallout of the Log4Shell vulnerability accelerated efforts to require a software bill of materials (SBOM) for the apps, libraries and other digital tools we rely on, but when it comes to generating and using this information, obstacles abound.
May 08, 2022
Most of the code in typical applications comes from open-source projects, importing dozens — and often, hundreds — of components created by volunteers. As the Log4j incident shows, those deep dependencies can carry critical vulnerabilities.