Destructive malware is back in Ukraine. Will it usher in cyberconflict?

The WhisperGate malware masquerades as ransomware but really breaks computer files beyond repair.
The discovery of a damaging hacking tool in Ukraine last week is sounding alarms across the global cybersecurity community and adds to Kyiv’s grim history as a testing ground for new forms of digital mayhem.
The so-called “WhisperGate” malware — as Microsoft named it after uncovering the malicious software in dozens of Ukrainian targets — may very well pose a threat to the U.S. Although WhisperGate’s capabilities and origins are still coming into focus, it’s hard to shake a sense of cyber déjà vu as parallels emerge with the NotPetya malware that wreaked havoc on global networks five years ago.
WhisperGate is designed to inflict maximum damage on systems it infects, and some experts warn it could be modified to spread quickly. Its appearance as Russia amasses tens of thousands of troops along Ukraine’s borders could be seen as a morale-sapping precursor to a widespread invasion — and doesn’t bode well for the future of cyberconflict.
“With the geo-political tensions going on in that particular region and different parties involved, this kind of attack can easily be adapted/changed towards a self-distributing malware attack with global impact,” Christiaan Beek, senior director and lead scientist at cybersecurity firm Trellix, told README in an email.
Trellix researchers categorized WhisperGate as “pseudo ransomware” in a blog post yesterday detailing what it does. Once executed, the malware rewrites the Master Boot Record on victim machines before rebooting them with a link to a Bitcoin wallet and a ransom demand. Stage 2 of the attack downloads a file wiper via a content distribution network linked to popular chat application Discord, corrupting the contents of dozens of file types with no way to restore them.
Microsoft’s Threat Intelligence Center, which first uncovered WhisperGate in dozens of Ukrainian systems on Jan. 13, said it “assesses that the malware, which is designed to look like ransomware but lacking a ransom recovery mechanism, is intended to be destructive and designed to render targeted devices inoperable rather than to obtain a ransom.”
In other words, it’s “fake ransomware,” as Katie Nickels, director of intelligence at Red Canary, said in a virtual event Tuesday. “This pretends to be ransomware, but it’s actually just destroying things.”
Cybersecurity company CrowdStrike likened the technique to the NotPetya malware, which infected thousands of Ukrainian targets in 2017 before spilling beyond its borders and causing an estimated $10 billion in global losses.
“However, the WhisperGate bootloader is less sophisticated, and no technical overlap could currently be identified” with the Russia-backed group behind the NotPetya attack, CrowdStrike researchers noted in a blog post Wednesday.
Microsoft has attributed WhisperGate to the “DEV-0586” threat actor — a placeholder name for a group it has not yet linked to any other country or previously known pattern of hacking activity. But the wiper attacks coincided with a series of website defacements in Ukraine that Kyiv has pinned on a Belarus-linked threat group.
“Information operations are a regular feature of Russian and Belarusian cyber activity,” John Hultquist, vice president of intelligence analysis at cybersecurity company Mandiant, said in a blog post yesterday. “Russia and its allies will conduct cyber espionage, information operations, and disruptive cyber attacks during this crisis.”
The Cybersecurity and Infrastructure Security Agency called the WhisperGate discovery “particularly alarming” as it urged U.S. companies to boost their defenses against potentially damaging intrusions.
Others were circumspect. “[W]e see no reason to panic because of these events,” researchers with Cisco Talos said in a blog post today noting that the WhisperGate attackers likely had access to victims’ networks months in advance. “However, defenders around the world should carefully watch the situation in Ukraine, particularly after the global impact of the Ukraine-centric attack that was NotPetya.”
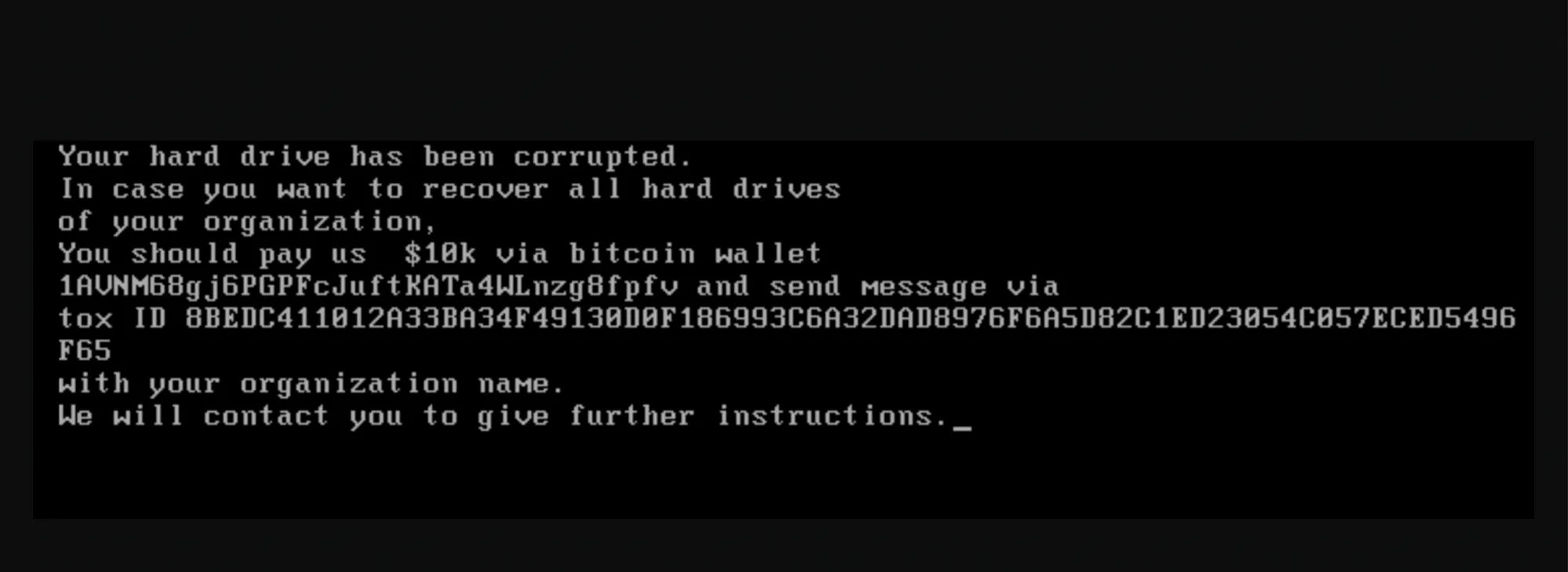 WhisperGate malware reboots victims’ computers with a fake ransomware message.
WhisperGate malware reboots victims’ computers with a fake ransomware message.War on the horizon?
Dmitri Alperovitch, chairman of the Silverado Policy Accelerator and former CTO of CrowdStrike, said the significance of recent cyberattacks to the wider Russia-Ukraine conflict may be overblown.
“Make no mistake about it: if there is an invasion, most of the action will be on the ground in meatspace with ground forces, with artillery, with rockets and missiles and the like, and an air campaign… cyber will at best play a very small, supporting function,” he said on the Politics + Media 101 podcast.
Alperovitch told README in an email that news of the WhisperGate malware hasn’t changed his assessment.
“We may very well see disruptive attacks like this against Ukrainian networks for tactical and psychological effect but the main action — if it does happen — will take place offline,” he said.
Nadiya Kostyuk, assistant professor of cybersecurity policy at the Georgia Tech School of Public Policy, said that although Ukraine has a reputation for being a “testing ground” for sophisticated malware, the recent combination of web defacements and fake ransomware is unlikely to play a major role in the wider conflict, in part because such attacks are difficult to pin on Russia and are unlikely to cross any red lines.
“We’re still figuring out how this ‘peace and war’ threshold will apply to cyber — and everyone agrees that it cannot apply in the same way [as kinetic warfare], because you cannot kill people through cyber means in most cases,” she told README. “It’s been a huge problem.”
Top U.S. intelligence officials and several cybersecurity companies have blamed Russia for unprecedented cyberattacks on Ukraine’s power grid in 2015 and again in 2016, which temporarily knocked out electricity for a few hundred thousand people in both cases.
“I do believe Russia is in the Ukrainians’ networks — but they’re keeping it really quiet,” Kostyuk said. “If they decide to invade, they will use the information and use this access to make victory swift; we could potentially see some more cyberattacks.”
As to whether Russia will order its nearly 100,000 troops near the border to attack? “I hope not, but it seems like everybody agrees that it’s just a matter of time,” she said.







