Postcards from Hacker Summer Camp 2023

Cynthia Brumfield
The promise and threat of artificial intelligence, government policy and some surprising revelations about the Viasat hack were among the major takeaways from Black Hat and DEF CON.
LAS VEGAS – Tens of thousands of hackers and security professionals descended on Sin City last week for the annual Hacker Summer Camp, a series of security-focused events centered on the Black Hat, DEF CON, and B-sides Las Vegas conferences.
Hundreds of speakers, security researchers and contest participants recapped their findings and unveiled flaws in dozens of technologies central to the digital economy and national security systems.
Here are some of the big themes emerging from this year's dizzying congregation of talks and demos:
Artificial intelligence everywhere
Not surprisingly, given the explosive emergence of Big-Tech-created AI chatbots this year, the most significant theme of the event was artificial intelligence.
"Yes, I'm completely burned out on the topic," Black Hat and DEF CON founder Jeff Moss said in kicking off the first of the two blockbuster conferences. "It's not going away, so I have to talk about it. This is me being forced to talk about it. What I find fascinating with AI, though, is that it's essentially prediction, and it's getting cheaper and cheaper to produce predictions. And so, if you think it's easy to create an AI model now, wait ten years."
In her opening keynote at Black Hat, Maria Markstedter, CEO and founder of Azeria Labs, warned that the gold rush surrounding AI models lacks security and safety guard rails. "As we all know, security slows down progress. Move fast, break things, that's the bottom. That's why products always initially lack security pitches." AI purveyors won't focus on security until hacks occur, she said. "Companies didn't just decide to invest into security on their own. Hackers forced them to," Markstedter said.

Kirsten Gibson
One of the most significant AI events was hosted by AI Village at DEF CON and backed by the federal government so that hackers could ferret out bugs in large language models built by Anthropic, Google, Hugging Face, Nvidia, OpenAI and Stability, with the winner landing a high-end Nvidia GPU. Although a high-profile event, organizers are unlikely to announce the contest winners for several months.
The biggest piece of AI news from the conferences was the Defense Advanced Research Projects Agency (DARPA) announcement of the AI Cyber Challenge (AIxCC) at Black Hat. The AIxCC contest will award $20 million to teams that best show how to use AI to develop state-of-the-art cybersecurity systems. "We need a forcing function, something that breaks together top thinkers like the ones in this room in both AI and cybersecurity to show how AI could be used for good, could be used to solve key challenges," Perri Adams, program manager in DARPA's information office, said in a surprise announcement following Black Hat's opening general session. "DARPA's AI cyber challenge will ask the best and brightest in AI and cybersecurity to defend the software on which all Americans rely," Adams said.
At DEF CON, Department of Homeland Security chief Alejandro Mayorkas raised the prospect of creating an AI safety review board on par with DHS's newly created Cybersecurity Safety Review Board (CSRB). "I think one of the things that we are looking at, without going too far ahead, is we don't have an AI safety review board just like our Cyber Safety Review Board that now issues very significant reports," including a just-released report on the teen gang Lapsus$ and one coming up on cybersecurity in the cloud.
Spot the feds
Mayorkas wasn't alone in bringing a federal perspective to Hacker Summer Camp: A spate of government officials showed up at Black Hat and DEF CON to weigh in on the top cybersecurity issues driving the U.S. policy agenda. Moss noted that their presence highlights how government officials "are starting to consult with our community a little bit more. This is sort of a dangerous period because if we [hackers] screw up the advice or we don't look like we're reliable, honest partners, we might not be asked to provide advice anymore."
"We've come a long way from 'spot the Fed' at DEF CON," Jason Healey, senior research scholar and adjunct professor at the School of International and Public Affairs, Columbia University, said before his keynote interview with Kemba Walden, Acting National Cyber Director in the Office of the National Cyber Director (ONCD) in the White House. Walden joked, "I'm not playing spot the fed because I'm the guy."
More seriously, she explained, "Congress passed a statute, they made a law that says that the White House has to have a durable presence thinking about strategizing for cybersecurity no matter what the administration." Walden stressed that one of the ONCD's superpowers is being able to crack open the budget and ensure the federal agencies get the cybersecurity funding they need.
Speaking alongside Victor Zhora, Ukraine's top cyber official, Jen Easterly, director of the Cybersecurity and Infrastructure Security Agency (CISA), said during an evening keynote session that Ukraine's cybersecurity battles with Russia are an example of the kind of resilience she has promoted to U.S. critical infrastructure.
"We know that given the state of networks today, the connectivity, the interdependence, the vulnerabilities that exist, technology is not secure by design," Easterly said. "We are very likely going to see attacks that cause great disruptions, and learning from you about the resilience and desire, the operational resilience, and frankly the societal resilience that you all have demonstrated in a shining example of unity fighting onto victory."
Bomb scare, packed hallways and badge grumbling
Both Black Hat and DEF CON garnered good vibes among the attendees. One possible exception was the venue for Caesar's Forum, where DEF CON held most of its track talks.
Some attendees complained that Caesar's Forum was uncomfortably small to accommodate the estimated 30,000 attendees, with almost impassable hallways for the track talks. README overheard one of the conference organizers say that they didn't know where to host the event next to overcome the situation. Despite possible overcrowding, an evacuation of Caesar's Forum following a bomb threat, which forced the cancellation of Saturday night activities, took place without a hitch, thanks to the legendary DEF CON goons.
Likewise, one village talk README attended at Harrah's was packed, with a line wrapped twice around a hallway, with some attendees unable to make the room capacity cut enforced by the goons.
Cynthia Brumfield
Another complaint was the lack of official DEF CON badges, famed for their ingenuity and value. One DEF CON attendee envied README's press badge, modeled on the official badge, and complained about his ordinary paper badge. The overproduction of badges in years past, combined with production and shipping shortages this year, apparently led to the shortage of official badges.
Significant incident and vulnerability revelations
No Black Hat or DEF CON would be complete without a few cybersecurity bombshells that shed light on significant incidents or uncover new vulnerabilities. This year's conferences were no exception.
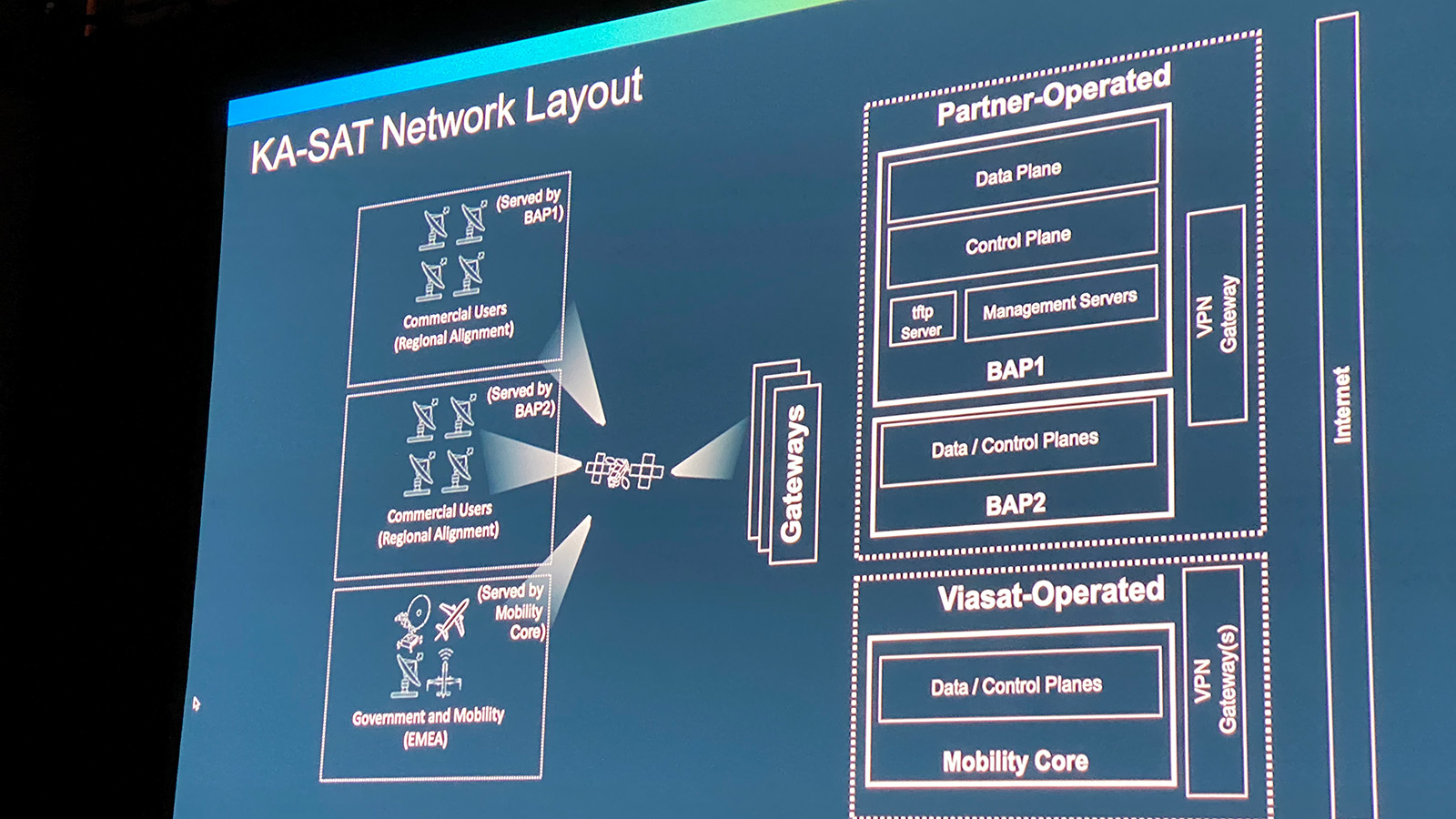
At Black Hat, Mark Colaluca, vice president and chief information security officer at Viasat Corporate, and Kristina Walter, formerly chief of Defense Industrial Base (DIB) Cybersecurity at the National Security Agency (NSA), delved into Russia's hack of the satellite internet services offered by Viasat that took out tens of thousands of government and private sector modems on February 24, the eve of Russia's war on Ukraine. (Later at DEF CON, Nick Saunders, Chief Cybersecurity and Data Officer, Viasat Government, got into the technical nitty-gritty of the incident).
Among the revelations in the Black Hat talk is that the day before the hack, failed attempts had been made using several sets of valid user credentials to hack into a Viasat VPN appliance. Just how the hackers gained the credentials is a mystery, and Colaluca said an ongoing investigation is underway.
Another bit of news Colaluca revealed: a second attack, aside from the well-known one that delivered wiper malware to the affected modems, created a denial-of-service situation when the attackers flooded Viasat with DHCP requests to kick customers offline.
Cynthia Brumfield
Colaluca said that part of the impetus behind his Black Hat talk was to dispel inaccurate speculation surrounding the Viasat hack. "There was a speculation about a zero-day vulnerability on a VPN appliance, so we just wanted to correct that," he told README. "And, at least to our forensic knowledge right now, a compromised software supply chain was not involved in any way, shape or regard. So, I believe our ability to communicate specific technical details now will help correct some of the early narratives."
Tomer Bar, VP of Research at SafeBreach and Omer Attias, a security researcher at SafeBreach, walked through how they created Defender-Pretender, manipulating Microsoft's Defender antivirus tool update process to sneak malware into systems. Microsoft patched the vulnerability that enabled the malware delivery in April 2023. "Please make sure that you are using this version of the malware protection platform or above," Bar told the attendees. "If not, you are vulnerable."







