Malware creators are relying on relatively uncommon programming languages such as Rust, Go, and Swift — and not just because they’re sick of writing code in C. Defenders have been forced to keep up.
From vulnerabilities in Starlink user terminals to fresh iCalendar exploits, this year’s Black Hat and DEF CON conferences offered a fount of cybersecurity knowledge for hackers, policymakers and everyone else who braved the Las Vegas heat and monsoon weather.
Is the world of blockchain as intimidating as it sounds? Information security consultant Jackie Singh interviewed Web3 security practitioners to get their perspectives on the challenges and opportunities in securing these new internet technologies.
README adapted this article from a January 2022 report by Matt Goerzen and Gabriella Coleman.
Cybercriminals are selling “exclusive” stolen data to multiple customers, threatening the stability of illicit marketplaces before even considering Justice Department actions.
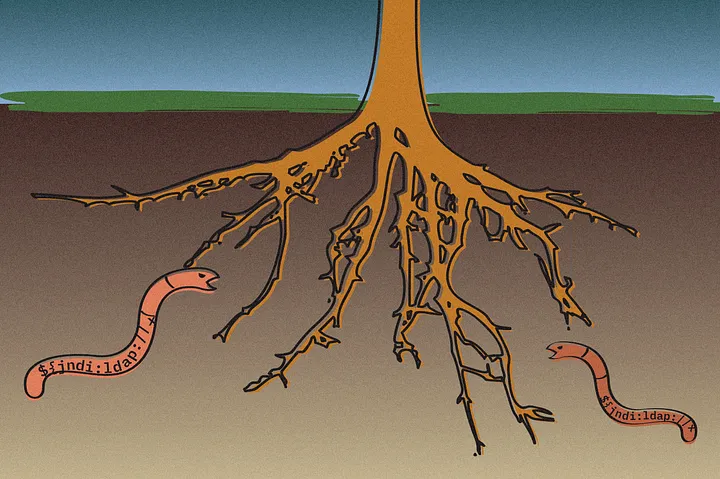
Most of the code in typical applications comes from open-source projects, importing dozens — and often, hundreds — of components created by volunteers. As the Log4j incident shows, those deep dependencies can carry critical vulnerabilities.
T-Mobile is the latest high-profile target of the Lapsus$ cybercriminal group, whose bar-brawl tactics have stoked tech industry fears of copycat attacks
There will be bumps on the road to securing this burgeoning ecosystem, where multimillion-dollar heists still happen with alarming frequency.
The buzzy ShmooCon cybersecurity conference returned this weekend after a pandemic hiatus, drawing a lively crowd of hackers, security practitioners and inside-the-Beltway types to downtown Washington, D.C.
Web3 technology offers a chance to break free from past cybersecurity mistakes — realizing that potential will require investment from passionate, curious, and open-minded information security professionals.